Bitcoin Best Security Practices: Multisig wallet with multiple hardware wallets of different manufacturers
Best security practices in bitcoin cold storage to avoid counter party risk associated with hardware and software wallets
It’s easy to get a software wallet today from your phone app store. Most people are content with keeping their crypto or bitcoins in their exchange like Binance or FTX.
However, time and time again we are reminded of the root cause that inspired the invention of bitcoin in the first place. If you read the bitcoin whitepaper and the reason why Satoshi Nakamoto worked on Bitcoin in the first place, you will realize that his main concern is the counter party risk associated with the current fiat money system.
“The root problem with conventional currency is all the trust that's required to make it work. The central bank must be trusted not to debase the currency, but the history of fiat currencies is full of breaches of that trust.” - Satoshi Nakamoto, 2009.
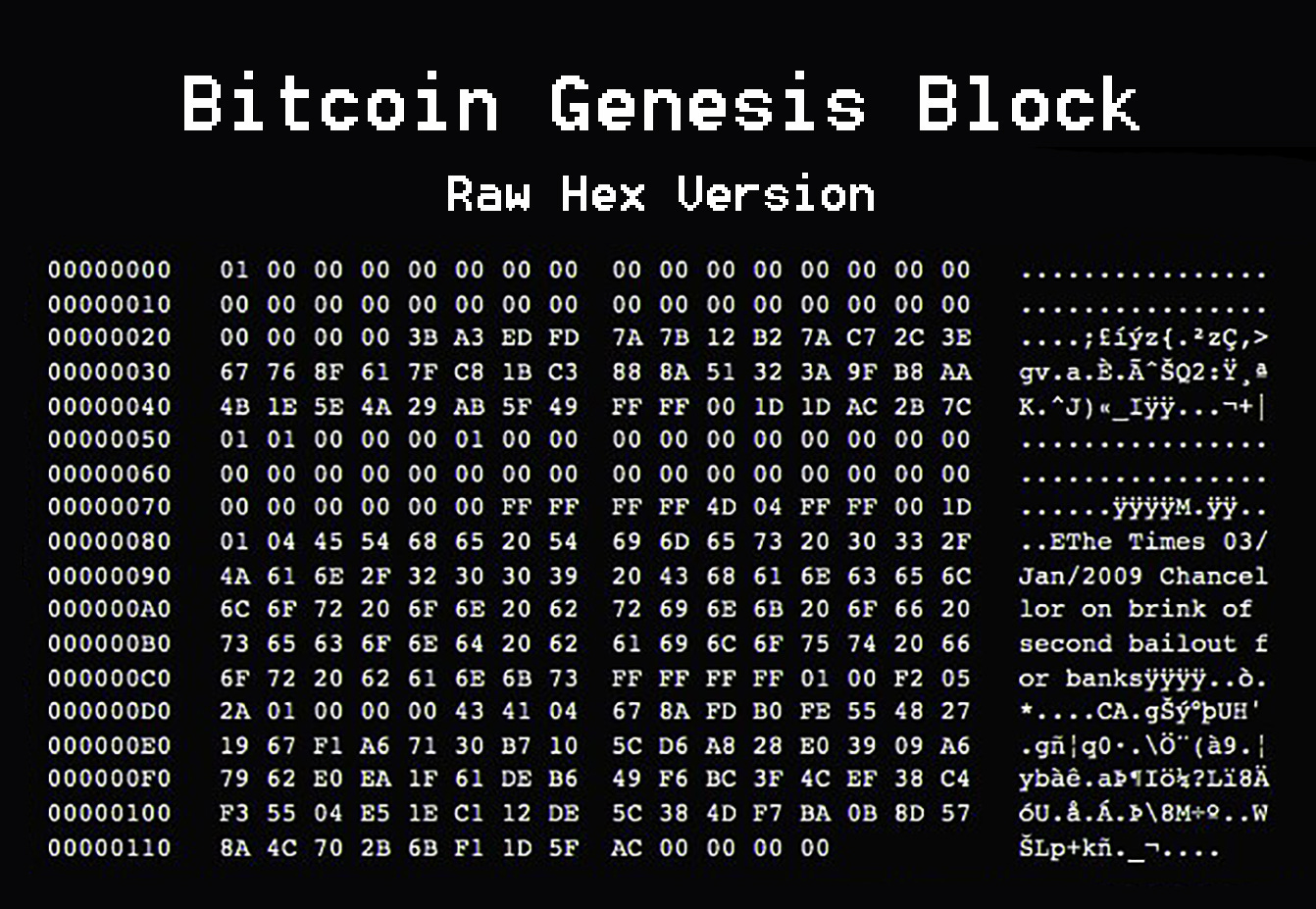
On the genesis block he inscribed below message that will remain there for eternity.
“The Times 03/Jan/2009 Chancellor on brink of second bailout for banks.” Reference: https://en.bitcoin.it/wiki/Genesis_block
Referring to the Times news paper headline on that day.
This refers to the constant debasement of currency caused by fractional reserva banking where banks commonly loan out their customers money with tiny fraction in reserve, and when those loans failed to get paid back due to failed business or mortgage, the whole economy and customer who take no part in those businesses suffer when the bank experiences bank run or running out of money, when this happens the central banks of any nation normally steps in and print money digitally or physically to backstop the banks’ losses, essentially removing the consequences of bad investment or loaning decisions by those banks. However this does not remove the negative impact of those failed loans, when central banks print money out of thin air in such cases, those money now flow into the real market and chases real goods and services, and since the goods and services cannot be printed out into existence by a mouse click as in fiat money, eventually the price of those goods and services will increase as more and more fiat money and funneled into the real market by the central banks through their commercial banks and other closely associated institutions that get those money first - due to their proximity with the money printer (ie. the central banks), this phenomena is known as the Cantillon effect, and those people can be called Cantillonaires.
Bitcoin is a computer software, much like your microsoft word or microsoft excel. It is run on volunteery basis by anyone on the planet who runs the bitcoin core software on their computers or laptops. The software keeps the ledger of transaction from the genesis block above up until now. In simple terms, the software is like an excel spreadsheet that contains who owns what and how much. However not everyone can write a new data into this spreadsheet, and not everyone can spend the bitcoin balance (UTXO) associated with each public addresses (wallets). Only those who know the private key of the associated wallets can spend the bitcoin contained in that wallet, because before the bitcoin can be sent to other address, the wallet owner has to prove that he has the private key, to do that he needs to sign the transaction, signing a transaction is giving a piece of data called ‘Signature’ that is created using the private key, the bitcoin network can verify this ‘signature’ that it was created using the valid private key without the private key being released or publicised, so from ‘signature’ alone one cannot derive the private key, but one can derive the conclusion that it was generated using valid private key, so no other person other than the person how know the private key created it. The technical process is explained in detail here: https://learnmeabitcoin.com/beginners/digital_signatures_signing_verifying
or here:
Digital Signature
My article is written in Indonesian but it can easily be translated to English without losing much of the nuances.
Once you understand the process of signature creation you will know that the bitcoin wallet is not a wallet, it has nothing in it, it is just a hardware that generates signature data that is used to verify a transaction. Why would we use a dedicated hardware for that? Because if we use our mobile phones or computers, our keyboard inputs and data that we copy and paste can easily be scooped by a spyware or malware or a random website that we accidentally open. The data can be released by mistake just like how people get their Facebook or Instagram account hacked because they accidentally leak their account password. Using a dedicated hardware that is separated from the computer or mobile phones reduce this risk, because the private key is never released outside of the hardware wallet device itself, the only data that gets sent out from that device is the digital signature which does not contain the private key, so it reduce or even eliminate the risk of you leaking your private key by accident while typing it on your laptop keyboard or mobile phones.
Some hardware wallets like Trezor works via USB connection with the computer, others can connect wirelessly via Bluetooth or camera by scanning QR code. In general all of these hardware wallets are secure, but wireless connection provides more confidence due to being airgapped with any external hardware, so that there is no chance that the hardware wallet itself can get hacked via its USB connection - even though this is very unlikely, and even if it does, it requires a very complicated and lengthy process like shown in this very interesting documentary about a hacker that managed to hack a hardware wallet (since then the hardware wallet has been upgraded so that the same hacking method doesn’t work anymore).
What
if the hardware wallet has a backdoor that no one knows about? Many of
these hardware wallets have been around for almost a decade, so in
general the longer that product has been around without any reported
breach or hacks, the more reliable they are. But of course as bitcoiners
often say, Don’t Trust, Verify! and Slay your Heroes!
So to combine the security of multiple hardware wallets while protecting ourselves from the risk of any one of that hardware being compromised (either by us or by the manufacturer), we can combine multiple hardware wallets made by different manufacturers to create a digital signature, essentially creating bitcoin wallet address by using multiple hardware wallets, this is called Multisig Wallet. We can use 2, 3 or more hardware wallets for this. For example a multisig that was created with 3 hardware wallets can be signed using any two of the 3 hardware wallets, or in any setup that you prefer based on the software. The software that we use can be varying, one of the most common ones are open sourced ones like Sparrow Wallet, or Electrum, etc.
By using multiple hardware wallets from different manufacturers, we ensure that if any one or two of those hardware wallet get compromised, we don’t risk losing our bitcoin, because for them to steal our bitcoin in a multisig wallet, all of the three, four, five or more of our hardware wallet have to be compromised, given that each of the hardware wallets come from different manufacturers from different countries by different people and companies who are competing against each other, the chance of all of them being compromised at the same time is very unlikely. Because even one hardware wallet brand or manufacturer being compromised hasn’t been heard of as of this writing, most of the hacking methods are very costly and require expensive equipment to do that, hence most of the time the hacking tutorials are for research and marketing purposes, for instance Ledger manufacturer posted about how to hack a Trezor wallet, with equipment costing millions of dollars.
https://blog.ledger.com/Breaking-Trezor-One-with-SCA/
Most of the time the hack happens on exchange, emails, websites or apps associated with cryptocurrency, because it is much easier that way. For instance, there are many bots sweeping github.com for any private key that is accidentally copied and pasted or written in there, if the wallet of that private key has balance, the bot will steal it automatically in milliseconds, and there are many bots that secretly scoops the data that you copied onto your clipboard, when you click copy to a text or numbers on your PC/phone, that data is now on your clipboard, and this data can be scooped up by websites that you are browsing.
Hardware wallet manufacturers attacking each other is a good and healthy thing, because that will ensure that the security tech in those hardware are constantly put to tests and being improved over time. Besides, they need direct access to the hardware to do the attack. So, from users point of view, as long as the hardware wallet is in secure location, there is very little chance that an attack live above can be perform on our devices. A physical access to the hardware is needed in such attack because the private key is stored in an encrypted form in the hardware wallet’s memory. This is why some hardware wallets like Coldcard and Ledger offered products with Secure Element which is a chip that’s harder to hack than the average chips.
While Trezor and Blockstream Jade do not use a secure element, it is important to note that secure elements are not a panacea for security. Secure elements can be compromised, and they can also introduce new vulnerabilities. Trezor's and Blockstream Jade’s security model is designed to be secure even without a secure element.
Bitcoin hardware wallets store private keys securely in their chips using a variety of techniques, including:
Secure key generation: Private keys are generated using a secure hardware random number generator (HRNG). This ensures that the private keys are truly random and cannot be predicted.
Key isolation: Private keys are stored in a secure enclave on the chip that is isolated from the rest of the device. This prevents malware or other unauthorized software from accessing the private keys.
Key encryption: Private keys are encrypted using a strong encryption algorithm. This makes it very difficult for attackers to steal the private keys even if they have physical access to the device.
PIN protection: The device is protected by a PIN code that must be entered before it can be used. This prevents unauthorized users from accessing the device and its contents.
Firmware signing: The device's firmware is signed with a secure key. This ensures that the firmware has not been tampered with and that it is the genuine firmware.
In addition to these security features, hardware wallets also typically have a number of physical security features that make it difficult for attackers to tamper with the device. For example, the chips may be tamper-proof or may be designed to self-destruct if they are tampered with.
As a result of these security features, hardware wallets are a very secure way to store private keys. It is very difficult for attackers to steal private keys from a hardware wallet, even if they have physical access to the device.
Here are some specific examples of how different hardware wallets store private keys securely:
Trezor wallets use a secure microcontroller (MCU) that has a dedicated secure enclave for storing private keys. The private keys are never exposed to the main processor of the MCU, which helps to protect them from malware.
Ledger wallets use a secure element (SE) that is a dedicated chip designed for storing cryptographic keys. The SE is certified to meet Common Criteria EAL5+ security standards, which is a high level of security.
KeepKey wallets use a combination of a secure MCU and a secure element. The private keys are generated in the secure MCU and then stored in the secure element. This provides a high level of security for the private keys.
Overall, hardware wallets are a very secure way to store private keys. The combination of security features makes it very difficult for attackers to steal private keys from a hardware wallet.
How the hardware wallets create private key is itself an interesting topic to dig into, I have written about it here (It’s in Indonesian, can be translated to English easily):
ENTROPY
In short, the hardware has entropy generator, basically a set of random numbers generated from various parts in the hardware, it took these random numbers and combine them into even more random numbers and then convert this final random number into a private key in the form of 12 or 24 seed phrase following the Bip39 standard.
A BIP39 seed phrase is a list of 12, 18, or 24 words that can be used to generate a cryptocurrency wallet. The security of a BIP39 seed phrase is based on the number of words in the phrase. A 12-word seed phrase has 128 bits of security, while a 24-word seed phrase has 256 bits of security.
For comparison, the security of a Bitcoin private key is 256 bits. This means that a brute-force attack on a 24-word BIP39 seed phrase would be as difficult as a brute-force attack on a Bitcoin private key.
In practice, a BIP39 seed phrase is very secure. The number of possible combinations for a 12-word seed phrase is 2048^12, which is a very large number. Even with the most powerful computers available, it would take billions of years to brute-force a 12-word seed phrase.
However, it is important to note that the security of a BIP39 seed phrase depends on how it is stored. If a seed phrase is stored in a digital format, it is vulnerable to theft or loss. For example, if a seed phrase is stored on a computer that is infected with malware, the malware could steal the seed phrase.
To improve the security of a BIP39 seed phrase, it is best to store it in a physical format. For example, a seed phrase can be written down on a piece of paper and stored in a safe place. Alternatively, a seed phrase can be engraved on a metal plate.
By storing a BIP39 seed phrase in a physical format, it can be protected from theft or loss. This makes a BIP39 seed phrase a very secure way to store cryptocurrency.
In addition to storing a seed phrase securely, it is also important to be aware of the risks of phishing attacks. Phishing attacks are attempts to trick users into revealing their seed phrases. For example, a phisher might send an email that appears to be from a legitimate cryptocurrency company. The email might ask the user to enter their seed phrase into a website. If the user enters their seed phrase into the website, the phisher will be able to steal their cryptocurrency.
To avoid phishing attacks, it is important to be aware of the signs of a phishing attack. Phishing emails will often contain misspellings or grammatical errors. They may also ask for personal information, such as a seed phrase. If you receive an email that you are unsure about, it is best to contact the company directly to verify that the email is legitimate.
By following these security tips, you can help to keep your BIP39 seed phrase safe.
Below is a step by step instruction on how to create a Multisig wallet using Sparrow wallet with Trezor, Blockstream Jade, and Coldcard.
To create a multisig wallet on Sparrow wallet with Trezor, Blockstream Jade, and Coldcard, follow these steps:
Open Sparrow wallet and create a new wallet.
Select the "Multisig" option.
Enter the number of signatures required for transactions.
Click the "Add Cosigner" button.
Select the "Hardware Wallet" option.
Connect your Trezor device.
Follow the on-screen instructions to generate a public key for your Trezor device.
Click the "Add Cosigner" button.
Select the "Hardware Wallet" option.
Connect your Blockstream Jade device.
Follow the on-screen instructions to generate a public key for your Blockstream Jade device.
Click the "Add Cosigner" button.
Select the "Hardware Wallet" option.
Connect your Coldcard device.
Follow the on-screen instructions to generate a public key for your Coldcard device.
Click the "Create Wallet" button.
Sparrow wallet will generate a multisig wallet address. You can now send and receive Bitcoin to this address. To spend Bitcoin from the multisig wallet, you will need to sign the transaction with the required number of cosigners.
For example, if you created a 2-of-3 multisig wallet, you will need to sign the transaction with two of the three cosigners. You can do this by connecting the appropriate hardware wallets to Sparrow wallet and following the on-screen instructions.
Multisig wallets are a secure way to store Bitcoin. By requiring multiple signatures for transactions, multisig wallets make it more difficult for attackers to steal Bitcoin.
Here are some additional tips for creating and using multisig wallets:
Use a different hardware wallet for each cosigner. This helps to prevent a single point of failure.
Keep your seed phrases safe. If you lose your seed phrase, you will lose access to your Bitcoin.
Be aware of the risks of phishing attacks. Phishing attacks are attempts to trick you into revealing your seed phrase.
By following these tips, you can help to keep your Bitcoin safe.
The
best way to keep seed phrase is by stamping them on metal plates and
keep it in a tamper proof bags and store it secretly in multiple
locations. For example if you use 24 seed phrase, store 12 words in one
seed plate in location A, and the other 12 words on location B, or have
one of it with you at all times. Ensuring that even if you die, nobody
can access your private key. In fact, dying with your private key remain
hidden is a generous philanthropic act, because the bitcoin disappears
with you, it will never re-enter the circulation, thus reducing the
amount of total supply in the market, making bitcoin even more valuable,
therefore increasing the wealth of the bitcoin holders who are still
alive. Of course you can inherit it to your loved ones as well, in that
case maybe you can give clues or information about the locations to
them, so that in case you die, they can have your bitcoin. Or you can
share 3 different hardware wallets between three family members and set
up a multisig wallet that way, so the only wat to spend the bitcoin in
that wallet is any two members have to agree to be able to initiate a
transaction. In that case if any one of the family member dies, the
bitcoin can still be retrieved by the living ones. The similar set up
can be used in a federated organization or corporation, for instance, we
can buy 5 different hardware wallets of different brands, and
distribute each to each of the Directors or stake holders in that
organization, use the 5 wallets to create a multisig wallet, so now that
wallet cal receive bitcoins from various sources, but the only way for
it to be spent is any 3 of the 5 members have to agree to initiate
transaction using their respective hardware wallets to sign the
transaction. This can be very useful to develop a trustless system in
such environment, so that the organization does not fall into the hands
of any particular leader in that group, because each leader will have
exactly one vote regardless of who they are. Each 5 directors with their
respective hardware wallet will have exactly equal power in this setup.
Enjoy your Bitcoin Learning Journey! Cheers!
https://samnawfal.blogspot.com/2022/01/memahami-bitcoin-part-1.html


Comments
Post a Comment